Dmz Network Diagram
In a dmz demilitarized zone network. The main purpose of a dmz is to protect the lan from the publicly accessible internet hosts on your network.
 Public Dmz Network Architecture Information Security Stack
Public Dmz Network Architecture Information Security Stack
Diagram of a typical network employing dmz using dual firewalls.
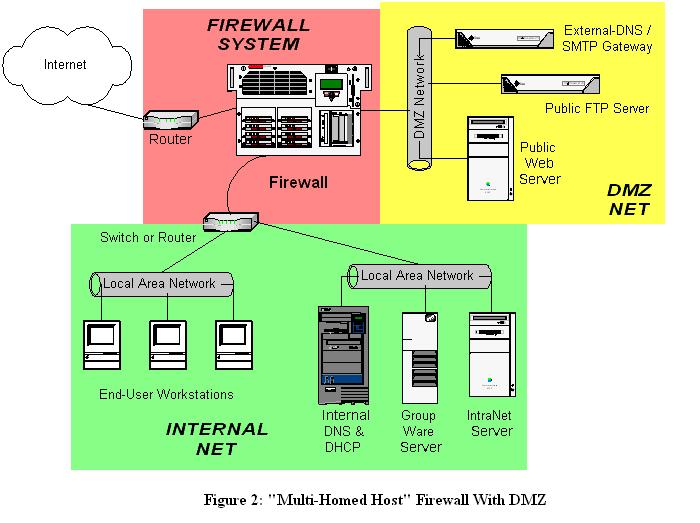
Dmz network diagram. Sangre viento grants anyone the right to use this work for any purpose without any conditions unless such conditions are required by law. In this diagram we have a packet filtering router that acts as the initial but not sole line of defense. Demilitarized zone dmz is a host or network segment located in a neutral zone between the internet and an organizations intranet private network.
Directly behind this router is a proper firewall. This work has been released into the public domain by its author sangre viento at english wikipediathis applies worldwide. You can edit this network diagram using creately diagramming tool and include in your reportpresentationwebsite.
In computer networks a dmz demilitarized zone is a physical or logical sub network that separates an internal local area network lan from other untrusted networks. 222 the three homed. Types of firewall and dmz architectures.
So if we dont block traffic from the dmz to the lan the dmz is basically useless. The example of the network diagram below shows network architecture with configuration usually called two firewall demilitarized zone. In some countries this may not be legally possible.
This way if one of them were to be compromised your lan still has protection from the attacker. In this case a sun sparcstation running say red hat linux with iptables. The second firewall also called back end or.
In computer networking a demilitarized zone is a special local network configuration designed to improve security by segregating computers on each side of a firewalla dmz can be set up either on home or business networks although their usefulness in homes is limited. A network diagram showing simple dmz. The first firewall also called the front end or perimeter firewall must be configured to allow traffic destined to the dmz only.
Stack exchange network consists of 175 qa communities including stack overflow the largest most trusted online community for developers to learn share their knowledge and build their careers. What is a dmz in the simplest of examples. Ask question asked 8 years 4 months ago.
The most secure approach according to colton fralick is to use two firewalls to create a dmz.
Security Zone Configuration Example
 Network Level Dmz Connectivity Architecture
Network Level Dmz Connectivity Architecture
 The Network Diagram Presented Below Is For A Local
The Network Diagram Presented Below Is For A Local
 Perimeter Network An Overview Sciencedirect Topics
Perimeter Network An Overview Sciencedirect Topics
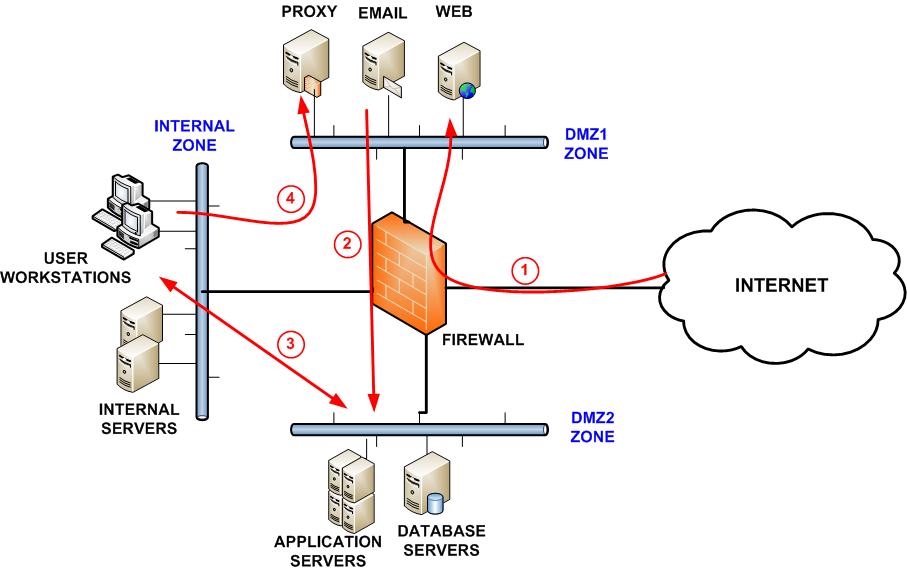 Network Segmentation Best Practices To Improve Security
Network Segmentation Best Practices To Improve Security
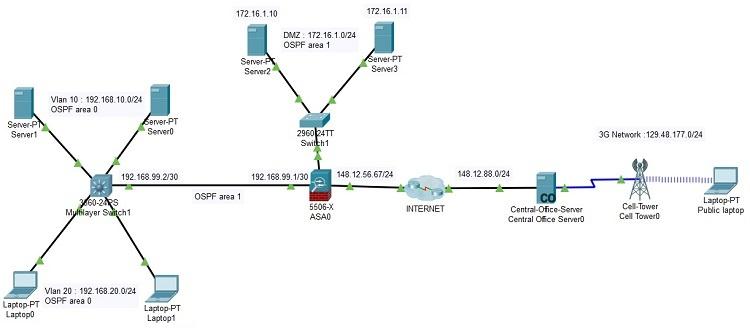 Packet Tracer Lab 18 Asa 5506 X Dmz Configuration Packet
Packet Tracer Lab 18 Asa 5506 X Dmz Configuration Packet
 Designing And Using Dmz Networks To Protect Internet Servers
Designing And Using Dmz Networks To Protect Internet Servers
File Dmz Network Diagram 1 Firewall Svg Wikipedia
 File Dmz Network Diagram 2 Firewalls Png Wikimedia Commons
File Dmz Network Diagram 2 Firewalls Png Wikimedia Commons
 Visio Stencils Basic Network Diagram With 2 Firewalls
Visio Stencils Basic Network Diagram With 2 Firewalls
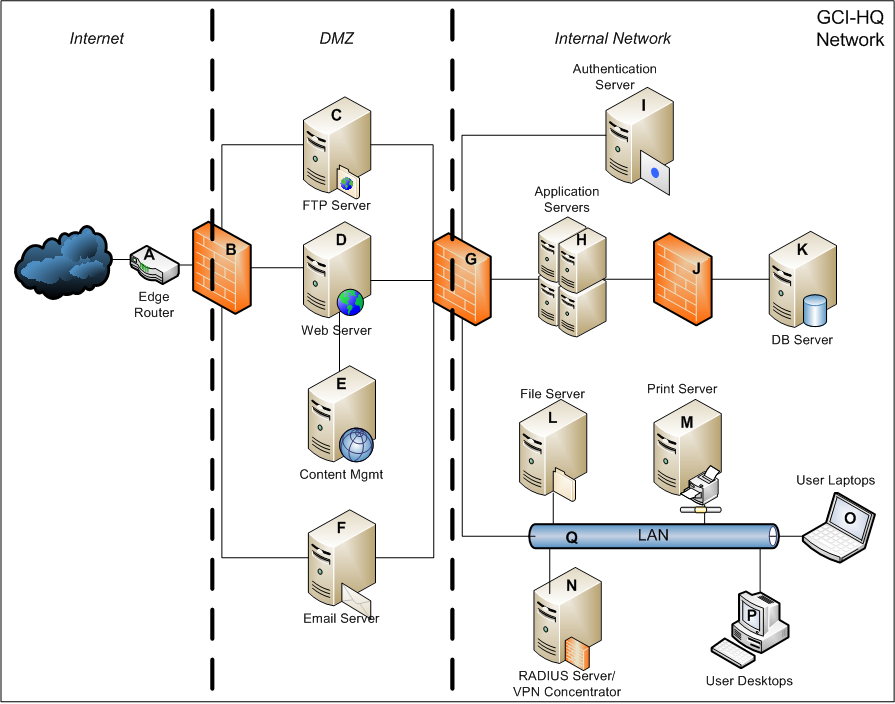 Solved Please Refer To The Accompanying Network Diagram A
Solved Please Refer To The Accompanying Network Diagram A
 Perimeter Network An Overview Sciencedirect Topics
Perimeter Network An Overview Sciencedirect Topics
 Dmz Network Diagram Unique Create An Azure Virtual Machine
Dmz Network Diagram Unique Create An Azure Virtual Machine
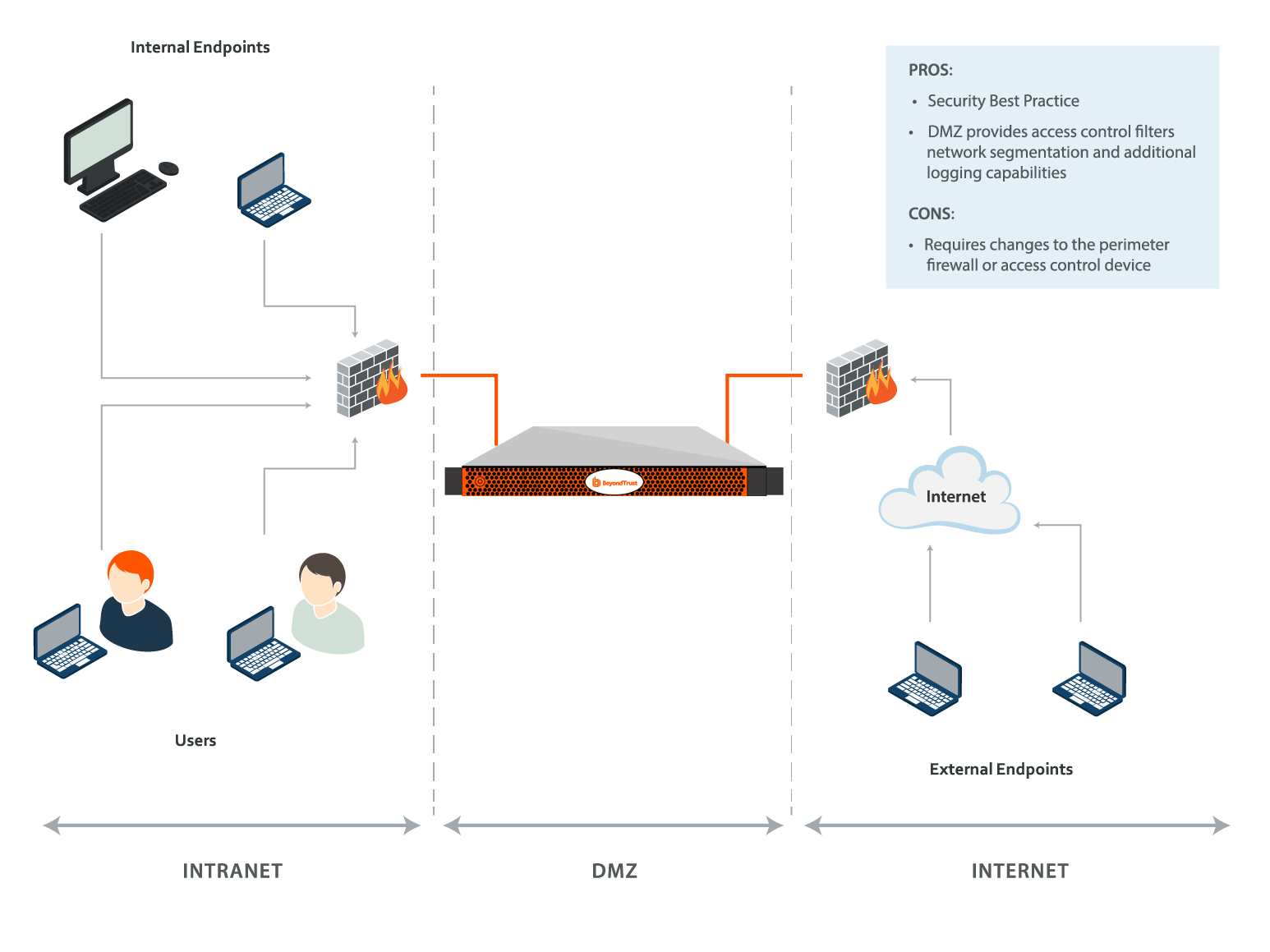 Secure Remote Access Appliance Network Infrastructure
Secure Remote Access Appliance Network Infrastructure
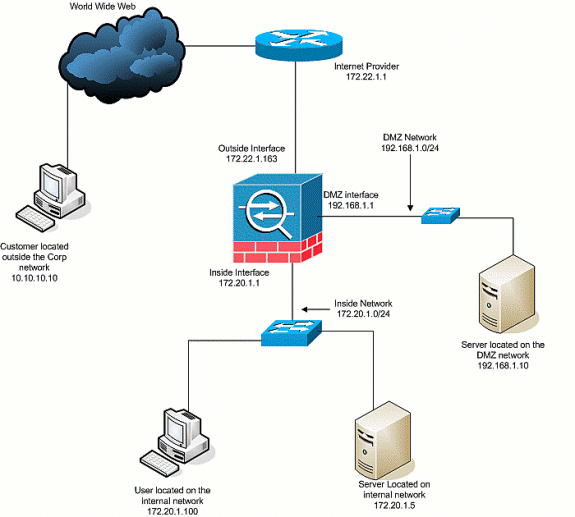 Pix Asa 7 X Enable Disable Communication Between Interfaces
Pix Asa 7 X Enable Disable Communication Between Interfaces
 Public Dmz Network Architecture Information Security Stack
Public Dmz Network Architecture Information Security Stack
 Dmz Network Diagram Luxury Sip Based Voip Circular Flow
Dmz Network Diagram Luxury Sip Based Voip Circular Flow


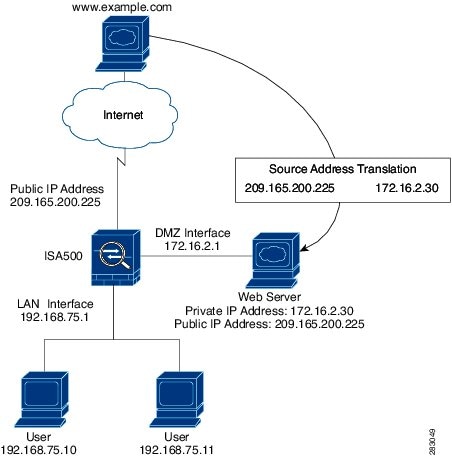


0 Response to "Dmz Network Diagram"
Post a Comment